Spy to Viber users (authentication bug) [solved]
Edited: I informed Viber on 26/06/2013 and they solved the bug in less than 12 hours.
 A few days ago I thought of analyzing some applications for mobile instant messaging, to see if they had security bugs. Initially my intention was to look for on the PC versions of Line and Viber, and I started by the latter.
A few days ago I thought of analyzing some applications for mobile instant messaging, to see if they had security bugs. Initially my intention was to look for on the PC versions of Line and Viber, and I started by the latter.
Analyzing the authentication process PC application of Viber I found several security flaws that allow to guess the PIN that gives access to Viber account from the computer with all that this implies: spying conversations in real time (images sent included), spy call history, impersonate, and access to address book. All this without the “victim” being aware practically nothing: receives only once a message on Viber (mobile) with a PIN.
More or less the authentication process is as follows …
Install Viber application for PC and at run it asks if you have a mobile (no matter the platform) with Viber installed. You say yes and it asks the mobile number, write it and Viber will send a message to mobile Viber app with a 4-digit PIN, which you must write on PC application and you will have Viber authenticated on your computer. The first error is clear: a 4-digit PIN?, is totally inadequate from the point of view of security.
Internally what the application after entering your mobile number on the PC (first step) does is to generate a string (pseudo)random of 40 characters long that will be used later as a key to identify your Viber account. This is made by the program itself without talking to the server, with the following HTTPS request:
<RegisterUserRequest>
<PhoneNumber>660100200</PhoneNumber>
<PushToken></PushToken>
<CountryIDDCode>34</CountryIDDCode>
<UDID>27b828c2768a7d7b65cg7dced6icb2aa90420c29</UDID>
<DeviceType>Desktop</DeviceType>
<SystemVersion>NT6.1</SystemVersion>
<System>Windows</System>
<ViberVersion>3.0.1</ViberVersion>
<SecondaryDevice>1</SecondaryDevice>
</RegisterUserRequest>
If you intercept the UDID (on your computer), then you can calculate the PIN that has reached the Viber application on mobile. Each time the PC application attempts to validate a PIN is making an HTTPS request as follows:
<ActivateUserRequest>
<UDID>27b828c2768a7d7b65cg7dced6icb2aa90420c29</UDID>
<ActivationCode>1234</ActivationCode>
<ProtocolVersion>14</ProtocolVersion>
<System>Windows</System>
</ActivateUserRequest>
It re-uses the UDID, and it tries to validate the PIN 1234. Viber (server side) has a protection that if you put the wrong PIN 3 times the system blocks, the problem is that you can jump it. Probably because the system uses a MySQL database and the UDID is stored in a field of type VARCHAR (or other non-binary), the comparison no distinction if you add blank spaces at the end of the UDID or if you change a lowercase/uppercase. Therefore, with this little trick you can send many more attempts and not just 3.
The UDID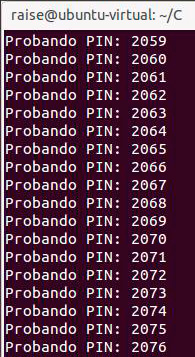 that server accepts has a maximum length, so you can not add spaces to infinity. But considering that server accepts 3 attempts per UDID, you can add enough blank spaces (over 300) and you can play with lower / upper case: the result is that as long as the UDID has 8 letters is enough to reach the UDID 9000 different combinations to test all possible PINS (in the tests I’ve done always generates a UDID with more than 8 letters).
that server accepts has a maximum length, so you can not add spaces to infinity. But considering that server accepts 3 attempts per UDID, you can add enough blank spaces (over 300) and you can play with lower / upper case: the result is that as long as the UDID has 8 letters is enough to reach the UDID 9000 different combinations to test all possible PINS (in the tests I’ve done always generates a UDID with more than 8 letters).
I made a small little program that tests all PINS, from 1000 to 9999, takes just under 2 hours to try them all. Once the PIN and a key is returned by the server, you have to intercept the request does Viber for PC and modify the response with a proxy like Burp Suite (the PIN is invalid since you’ve already validated previously with the request to see if it was correct). Once this is done you get full access to Viber account from your computer.
Should be noted that Viber on PC will not retrieve messages and call history made before that moment, but it will start to sync from then on.